Cybersecurity Support Deployments: An emerging cooperative approach
Policy Brief
Executive Summary
Purpose of this report
Governments worldwide are increasingly acknowledging the necessity of collaborative and partnered approaches to enhance cybersecurity. The scarcity of cybersecurity professionals and the dispersion of information among stakeholders in the government and the private sector have amplified the need for cooperation between governments and non-government entities. Various forms of cooperation have emerged, including information-sharing agreements, the exchange of liaison officers, and the establishment of task forces. In this context, this paper explores a particular form of cooperation that can be considered a type of “deployment”. Originally a military term, deployment refers to “the movement of troops or equipment to a place or position for military action.” Although governments have increasingly turned to this approach in recent years, it remains a relatively understudied method of collaboration, and its characteristics and dynamics have analytically hardly been understood. To analyze this tool in the field of cybersecurity, the working definition of “cybersecurity support deployment” in this paper is as follows:
Requesting support from other countries for matters of national security and inviting their experts can be sensitive issues for governments. This form of support has therefore been discussed, developed, and applied by practitioners, and its implementation mostly occurred behind the scenes, away from public scrutiny. However, insufficient knowledge and misunderstandings of the concept of deployment missions in public can lead to general suspicion, and aggressive narratives can raise fears of escalation in the context of conflict. This has especially been the case with deployment missions to Ukraine.
Consequently, governments have increasingly opted to share information about their deployment missions, aiming to demonstrate that they serve diverse purposes and unfold in various political contexts, many of which are civilian rather than military. In this paper, we draw on publicly available information to explore deployment missions.
It attempts to address the definitional blurriness of the concept and refines the tool for cybersecurity support deployments. To this end, we have compiled a list of 16 deployment cases from recent years (provided in the annex), [1] which have been analyzed using a purpose-developed framework.
Key findings
The utilization of deployments as a means of enhancing cybersecurity is communicated by some countries through proactive inclusion in strategic and policy documents or cooperation agreements. However, these communications primarily focus on the overarching goals of deployments without delving into the specific details of individual missions. Detailed information, such as deployment activities, the resources involved, and team configurations, is typically shared after the fact through press releases, via media coverage, or at cybersecurity events. This approach is largely driven by strategic considerations. Governments are cautious about revealing their intent to adversaries, as public disclosure could prompt them to remove their adversarial capabilities, enhance their concealment of access, or learn from observing the deployed team, thus strengthening their ability to evade detection in the future.
- Governments generally view deployment as one of several tools at their disposal to improve cybersecurity.
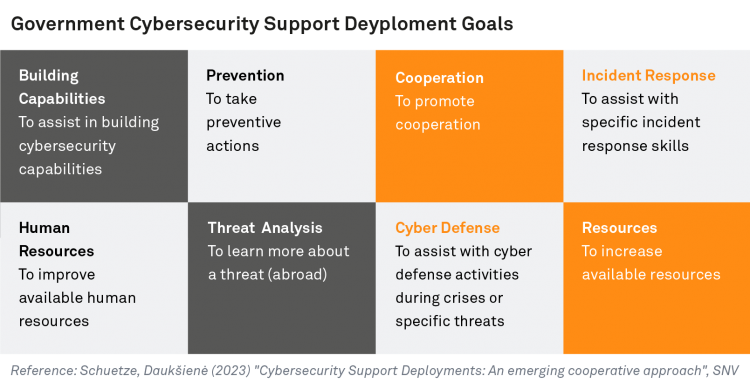
- Deployment is typically seen as a method for pursuing a variety of objectives in the fields of cybersecurity, cyber defense, and resilience, such as taking preventive action, assisting with incident response skills, and learning more about a threat actor.
- In addition to the objective of enhancing cybersecurity, deployments can serve other purposes, such as economic, national security, defense, or foreign policy considerations. For example, governments utilize deployments to foster cooperation and at the same time, prevent cyber incidents.
- The specific objective of a deployment determines its unique configuration. For instance, capability-building deployments (in which one state enables another to conduct a vulnerability assessment) entail different requirements than scenarios in which a state simply requests that another perform a preventive activity without gaining the skills necessary for future endeavors. Consequently, different types of deployments, potentially involving distinct personnel and timing, are necessary to address these varying needs.
- Deployments can also aim to enhance another state’s capacity to perform specific tasks. For instance, in the aftermath of a specific incident, a government may seek to acquire a particular capability to bolster its effectiveness in responding to similar situations.
- The cases examined also shed light on the diverse policy domains in which cybersecurity support deployments have been observed, including foreign policy, national security policy, and defense policy. In numerous instances, there are indications that deployments arise from long standing operational, policy, diplomatic, or military partnerships.
- Government entities assume various roles within deployments. They may serve as funders, providing financial support for the deployed resources. In addition, government staff can play a dual role, either by being deployed to execute specific activities or by overseeing the implementation of the deployed resources. Furthermore, certain government entities exercise a level of control, supervision, and instruction, directing or managing the deployed resources and/or activities.
- Examining the role of governments can provide insights into the setup of deployment missions, the involvement of non-government stakeholders, and the level of control exerted by the deploying government.
- The concept of “trust” is crucial in the context of cybersecurity deployments. Two dimensions are relevant: trust among government officials, which is necessary to facilitate deployments, and trust among professionals involved in implementing cyber activities during deployments. These dimensions are separate but can reinforce each other and interrelate, albeit through different mechanisms.
-
During deployments, capacity building takes place as teams engage in active implementation, allowing them to develop new skills and enhance their existing capabilities. This process applies to the supporting country and the supported country. Cybersecurity deployments are dynamic learning environments where continuous learning and skill development occur rather than mere provision-based arrangements.
Within the policy community, there is growing interest in cybersecurity support deployment. If such deployment missions are to become even more widely used, we recommend five practical considerations for governments, based on current empirical research:
- Consider the “Principle of Permission”
- Consider different forms of how permission can be granted
- Clearly state the need for cybersecurity support in the request
- Consider who could best provide the requested support
- Consider who should request support.
Furthermore, we recommend that countries considering the use of deployments in the future carefully consider their objectives and the specific contexts in which they intend to employ such missions. Policy makers should also give careful thought to how they can foster a sense of “personal trust” among the practitioners involved. This involves considering with whom and in what manner personal-level relationships can be established. For instance, forming joint teams and showcasing individual competences and skills can serve as effective trust-building measures before or during specific deployments. Additionally, practitioners should be actively engaged from the early stages of discussions surrounding potential cybersecurity support deployments.
To advance research in this field, we suggest that the analytical framework for cybersecurity support deployments developed in this paper be expanded. This can be achieved by incorporating additional dimensions, such as mapping the diverse legal frameworks that govern deployments, and by including more cases from a wider range of countries.
Julia Schuetze
Eglė Daukšienė