Government’s Role in Increasing Software Supply Chain Security: A Toolbox for Policy Makers
Policy Brief
Software has become a cornerstone of the systems that are essential to modern society. Like many other products, software is the result of complex international supply chains. There are unique characteristics of the software-developing ecosystem that make software supply chains particularly vulnerable: First, software-developing entities rely significantly on software components developed, delivered, and maintained by others. Besides this, software-developing entities often do not prioritize security when developing their products, which is why software-using entities often find it difficult to assess the security of a given software based solely on the information provided to them. In addition, the supply chain can be compromised at different stages of the software development life cycle, which makes securing software supply chains a tough challenge.
Software supply chain compromises such as SolarWinds or Log4Shell can have large-scale impact: an initial compromise of one entity in the chain violates the confidentiality, integrity, and availability of data further down the software supply chain, often affecting multiple organizations and sectors across national borders. Software supply chain compromises have led to, inter alia, ransomware operations on software-using entities and to the unauthorized access to sensitive customer data and proprietary source code. The perpetrators of such compromises are malicious actors with criminal, political and economic espionage, and sabotage objectives.
Given these threats, software supply chain security poses an urgent problem to policy makers. For too long, the issue has been seen mainly as a problem for vendors to resolve. But recently, policy makers have started to recognize that this field is also ripe for policy interventions, as shown by the US president’s 2021 Executive Order 14028 on Improving the Nation’s Cybersecurity and by the European Commission’s 2022 draft of the Cyber Resilience Act. Still, the possibility for government action for increasing software supply chain security extends further than the elements of these initiatives.
In this analysis, we develop a toolbox that combines diverse instruments with targeted government action to be practical guidance for policy makers. This toolbox approach has the advantage that policy makers can choose instruments suited to their respective positions, considering, for example, available resources and capabilities.
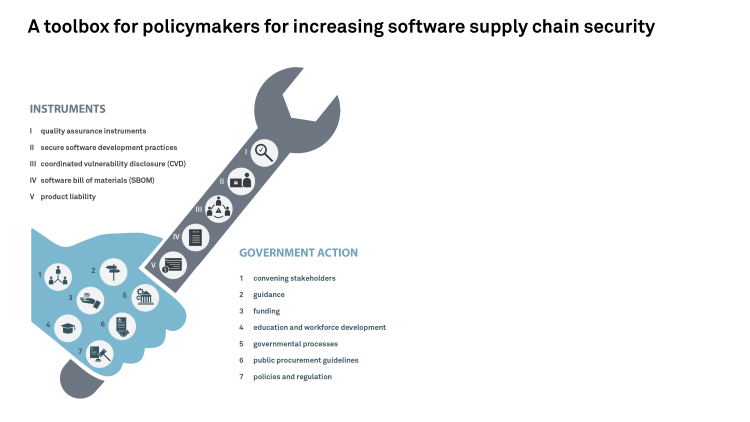
After reviewing the instruments and the possibilities for government action, we have compiled three sets of policy priorities that policy makers should focus on, providing three levels of ambition that cater to different national venture points.
Level 2 – Ambitious but Tried and Tested: Governments who want to take additional steps should focus on four actions. First, they should convene the national and international stakeholders involved in quality assurance instruments – that is, technical standards, quality assurance schemes, and product security labeling schemes – to allow for the coordination and exchange of good practices. Second, governments should issue guidance, tailored to the needs of different types of organizations including small and medium enterprises (SMEs), on how to implement secure software development practices.
Third, governments should adapt processes to require software-developing government agencies to develop and publish organizational CVD policies as well as require such policies from organizations supplying the public sector through public procurement guidelines. Fourth, governments should convene stakeholders to discuss challenges and solutions regarding SBOM use. These four actions can be implemented with limited resources and capabilities and within short to medium timeframes; they have also been implemented in different jurisdictions already.
Level 3 – Breaking New Ground: Governments who want to lead the way in increasing software supply chain security could explore five further actions. First, they could fund assessments of the effects of quality assurance tools on SSC security. Given positive results, they could fund the development of new technical standards or the adaptation of existing and relevant ones and establish a national – and ideally internationally harmonized – conformity assessment scheme and product security labeling scheme for software. Second, governments could develop regulation mandating software-developing
entities to implement secure software development practices. Third, governments could develop a national legal framework for CVD, which would require software-developing entities to put in place organizational CVD policies. Fourth, governments could fund the development and refinement of SBOM data formats and technical tools that build on SBOM data and develop regulation mandating SBOM use; for instance, starting with suppliers of critical infrastructure providers. Fifth, governments could develop a product liability regime that covers software (or amend an existing one to include software). When developing any regulation in this field, policy makers need to consider how such regulation will affect SMEs and individual developers, who typically have fewer resources and may therefore be disproportionately affected by regulatory burdens. These five ambitious actions would require significant resources and high capabilities and would take time to implement. In some cases, since good practices are not yet available, those actions would break new ground.
Whichever level policy makers choose, policies on software supply chain security will often be most effective when international coordination and cooperation are considered from the start. Emblematic examples of this include the harmonization of regulation on CVD to facilitate cross-border vulnerability disclosure or the international coordination of public procurement guidelines. In many cases, like-minded coalitions will provide the most promising starting point for international dialogue on these issues. Progress on this issue can also contribute to advancing multilateral cyber diplomacy. As all UN member states have already agreed back in 2015 that governments should take steps to increase the security of software and hardware supply chains, it is high time that policy makers act on this commitment by developing concrete national policies.
Dr. Alexandra Paulus and Christina Rupp